One of the many options and ways in which we can protect our Wi-Fi access point is MAC filtering. Like everything in the world of security, you must know that it is not impenetrable and that there are ways to skip this barrier that we add to our network, but without a doubt is one of the best options to increase the security of our network and Get anyone who does not want to connect to our access point.
MAC filtering takes its name from the Media Access Control (MAC) address of the network adapters of different devices that are ready to connect to a network, such as a computer, tablet or smartphone. Each device has a unique MAC address that identifies your network adapter- if we talk about a computer with multiple network cards will have several MAC address. It would be something similar to our identity card.
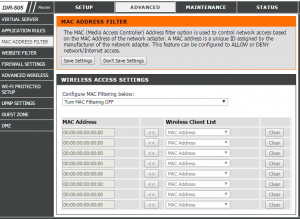
The MAC address filtering (Media Access Controller) option is used to control access, this is based on the MAC address of the network adapter. This function can be configured either to allow or deny access to the network. Also is considered “low security” because it is fairly easy to omit this filter, however, combined with other protocols can help improve security.
Find out information about how to open ICA file.
How does it work?
MAC filtering uses a list of MAC addresses that we will introduce, ie a list of devices. Taking this list into account, there are two modes in which you can configure:
Allowing the connection to the devices added to the list of MAC addresses, leaving any other without possibility to connect to our network. This is quite useful when we want only certain devices to connect to our Wi-Fi, but it has the disadvantage that if we receive guests we will not be able to use our network.
Denying the connection to the devices that appear in the list of MAC addresses, a circumstance in which any other device can connect. This form would be suitable to not allow the connection to a certain device of which we know the MAC address, for example, the mobile phone of our son or the equipment of the neighbor that connects to our network without permission.
Learn about how to open ICS file.
How to configure it
Configuring MAC filtering is quite simple. We must start by entering the router administration web. For this we must write the IP address of the router in our browser – that is the 192.168.x.x – and identify us with our credentials, which are usually admin as a user and as a password, although this depends on the router model we have.
Before proceeding with the configuration in the administration web, we must know the MAC addresses of the devices to which we want to allow or deny the connection. In the event that our goal is to deny the connection to a device that we do not own, we can use a program such as Wireless Network Watcher, with which we can see what devices are connected to our access point and MAC addresses.
Find out information about how to open RPMSG file.
Once you have entered the MAC addresses that will be used, we must go to the MAC filtering section. Among other configurations, we have to locate the Wireless or Wi-Fi section and enter the MAC filter submenu.